VMware Honeypot for Cybersecurity: My First Attempt into Building Defensive Tools so you can build your own too!
🛡️ Why Honeypots?
In the cyber wilderness, honeypots act like bait for hackers! so thats why we built VMware Honeypot for Cybersecurity 🎣 it allows us to…
🔍 Spot the Sneaky Ones: Honeypots help us identify and study potential cyber threats by luring in attackers.
💻 Learn and Adapt: They provide insights into attack methods, helping us fortify our defenses.
🚨 Early Warning System: Like a canary in a coal mine, honeypots alert us to malicious activity, allowing swift countermeasures.
🛡️ Prevention through Simulation: By mimicking real systems, honeypots help us understand and thwart attacks before they reach critical assets.
Whether you’re building your own honeypot or giving VMware Honeypot for Cybersecurity a try, you’re establishing a line of defense within your network—and hopefully picking up some new skills along the way! 😄
✨🌐 Features
Explore the magic of our VMware Honeypot, crafted to empower your cybersecurity arsenal with enchanting capabilities:
- 🖥️ Realistic Interface: Witness a user interface inspired by the vSphere Web Client, offering a convincing environment for potential attackers.
- 🤝 Basic Interaction: Engage with users through simulated endpoints, capturing minimal data such as IP addresses and timestamps.
- 🐍 Flask Python Backend: Powered by Flask, the Python web framework, our honeypot’s backend gracefully simulates basic endpoints.
- 🛡️ Security Measures: Designed with isolation and monitoring to prevent potential risks, your VMware Honeypot acts as a fortress against cyber threats.
- 📊 Analysis and Reporting: Harness the power of collected data for periodic analysis, gaining basic insights into emerging attack methods.
Prerequisites
- 💻 Operating System: Ensure you have a server or desktop (Windows/Linux) ready to host your cybersecurity tool.
- 🖥️ Web Dev Basics: Brush up on fundamental web development skills (HTML, CSS, JavaScript) for a seamless setup experience.
- 🐍 Flask Framework: Have Flask, the Python web framework, installed on your system.
In this tutorial, we will be demonstrating the setup of our Flask application on Windows.
Setup Steps
- 🌀 Clone the Repository:
- Start by cloning our GitHub repository containing the VMware Honeypot code.
- ⚙️ Install the Required Dependencies:
cd VMWare_honeypot pip install -r requirements.txt - ⚙️ Configure Flask Backend:
- Install Flask and other required dependencies using:
pip install flask
- Install Flask and other required dependencies using:
- 🚀 Run the Honeypot:
- Navigate to the project directory:
cd VMWare_honeypot - Run the honeypot:
python vmware.py
- Navigate to the project directory:
Usage
🔍 Once executed, ensure the server is running. Visit http://localhost:5000 – you will be redirected to the dummy VMware Sphere single sign-on page /ui/.
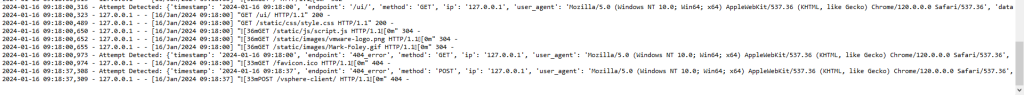
Here, when somebody attempts to log in, a message will be logged into honeypot.log with relevant information. Monitor login attempts here! 🖥️
Analysis
- 📅 Periodically review the honeypot.log file for insights into potential attack methods.
- 📊 Analyze IP addresses, timestamps, and any captured data to understand trends and patterns.
Credits
🙌 We appreciate the community support for feedback and improvement. Feel free to share your thoughts on our GitHub repository.
🎭 Mike Foley Humor: Utilizing some templating from Mike Foley Themes for comedic effect! 😄
Strengthen Your Cyber Defenses with VMware Honeypot for Cyber Security and strenghten your network today
By deploying a VMware honeypot, you’re taking a proactive step in safeguarding your digital assets. This clever decoy not only lures potential attackers away from your critical systems but also provides invaluable insights into their tactics and techniques.
Remember, in the ever-evolving landscape of cybersecurity, knowledge is power. By understanding the methods and motivations of those who seek to do harm, we can fortify our defenses and stay one step ahead.
Join the Fight Against Cyber Threats Today!
- Deploy Your Honeypot: Set up your VMware honeypot using the provided guide and start gathering valuable threat intelligence.
- Analyze and Adapt: Regularly review the data collected by your honeypot, identify emerging attack patterns, and adjust your security measures accordingly.
- Share and Collaborate: Engage with the cybersecurity community, share your findings, and learn from the experiences of others. Together, we can create a more secure digital world.
#VMwareHoneypot #CyberSecurity #HoneypotsForDefense
Join Our Community!
🌟 Get exclusive insights and the latest IT tools and scripts, straight to your inbox.
🔒 We respect your privacy. Unsubscribe at any time.




