Welcome to our comprehensive guide on 7-Zip Password Protection.
We will cover everything from locating and preparing your 7Z files for compression to creating strong, unbreakable passwords. You’ll also learn how to confidently adjust settings for optimal security and extract password-protected files when needed. Plus, we address common security concerns associated with 7-Zip, including its origins and how it compares to other file archiving tools like WinRAR, WinZip, Nanazip, and PeaZip. By the end of this guide, you’ll be well-versed in using 7-Zip for secure file compression and encryption, a vital skill in today’s digital world
Here’s my step instructions for using the 7ZIP.org tool to archive and password protect your files.
Step-by-Step Guide to Using
7-Zip Password Protection
1. Locate and Prepare Your Files: Start by finding the files or folders you want to secure.
Right-click your selection and choose “7-Zip” > “Add to archive…”.
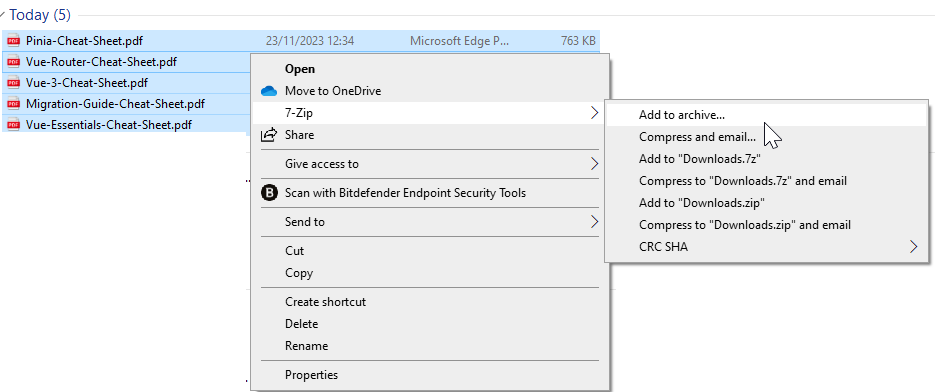
2. Selecting the Archive Format: While 7-Zip defaults to its native .7Z format, not everyone has the 7-Zip application to open this file type. For broader accessibility, you can choose the .ZIP format, which is more universally compatible.
3. Naming Your Archive: Enter your desired name in the “Archive name” field.
4. Setting Up Encryption: In the “Encryption” section, type in and confirm your password.
5. Choosing the Encryption Method: If you’ve chosen the .ZIP format and require strong security, switch the encryption method from the default ZipCrypto to AES-256. Be aware that this will necessitate the use of a file compression tool for extraction.
6. Finalizing the Archive: Click “OK” to create your encrypted .ZIP file with 7-Zip.
Important Note on Extracting Encrypted ZIP Files:
Please be aware that if you choose to secure your .ZIP files with the highest level of encryption, such as AES-256, Windows Explorer may not be able to open them. For extracting such strongly encrypted .ZIP files, you will need to use a dedicated file compression utility. Tools like 7-Zip or WinRAR are designed to handle AES-256 encryption and will enable you to safely access the contents of your encrypted archives.
Tips for Creating, sharing and storing Strong Passwords:
Creating a robust password is crucial when securing your files with 7-Zip. A strong password should be a complex mix of characters, numbers, and symbols, and it should avoid predictable patterns and common dictionary words. Aim for a password that is difficult to guess but that you can remember. Sometimes, you may need to share this password securely, especially if the encrypted file is for someone else.
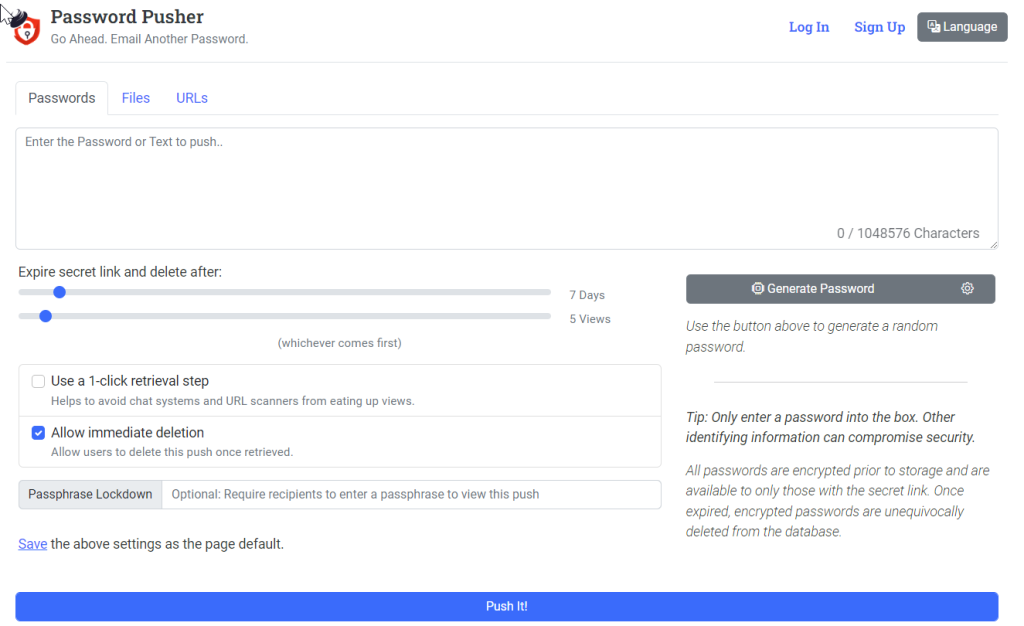
For securely sharing passwords over the internet, tools like Password Pusher offer a solution that protects sensitive information. Instead of sending passwords through potentially insecure channels like email or messaging apps, Password Pusher creates a secure, expiring link that can be used to transmit the password. You can set the link to expire after a certain number of views or a set amount of time, whichever comes first. This ensures that the password doesn’t remain accessible indefinitely, reducing the risk of unauthorized access.
Here’s how to use Password Pusher for your 7-Zip archives:
- Generate a Secure Password: Use Password Pusher’s “Generate Password” feature or create your own strong password.
- Configure Expiry Settings: Choose how long the link will remain active or how many views it will allow before expiring.
- One-Click Retrieval Step: Enable this option to help avoid premature link expiration due to web crawlers or accidental views.
- Immediate Deletion: Allow the recipient to delete the password link once retrieved for an extra layer of security.
- Passphrase Lockdown: For an additional security measure, you can require the recipient to enter a passphrase to view the password.
- Share the Link: Once the link is generated, send it to the intended recipient. They’ll have access to the password as per your configured settings.
By using Password Pusher, you can confidently share passwords for your 7-Zip encrypted files, knowing that the information is safeguarded against unauthorized access. Remember, never include the password in the same communication as the link to the encrypted file.
Extracting Files from Standard and AES-256 Encrypted ZIPs
For Standard ZIP Files in Windows File Explorer:
1. Locate Your ZIP File: Find the ZIP file in Windows File Explorer.
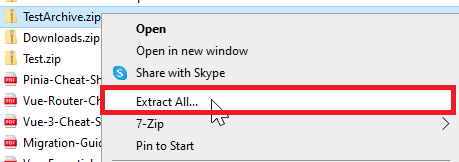
2. Extract the Files: Right-click on the file and select ‘Extract All…’.
3. Enter Password: If prompted, enter the required password for the ZIP file.
4. Choose Destination: Select a destination for the extracted files.
5. Complete the Process: Click ‘Extract’ to decompress the files to your chosen location.
If You Encounter an Error:
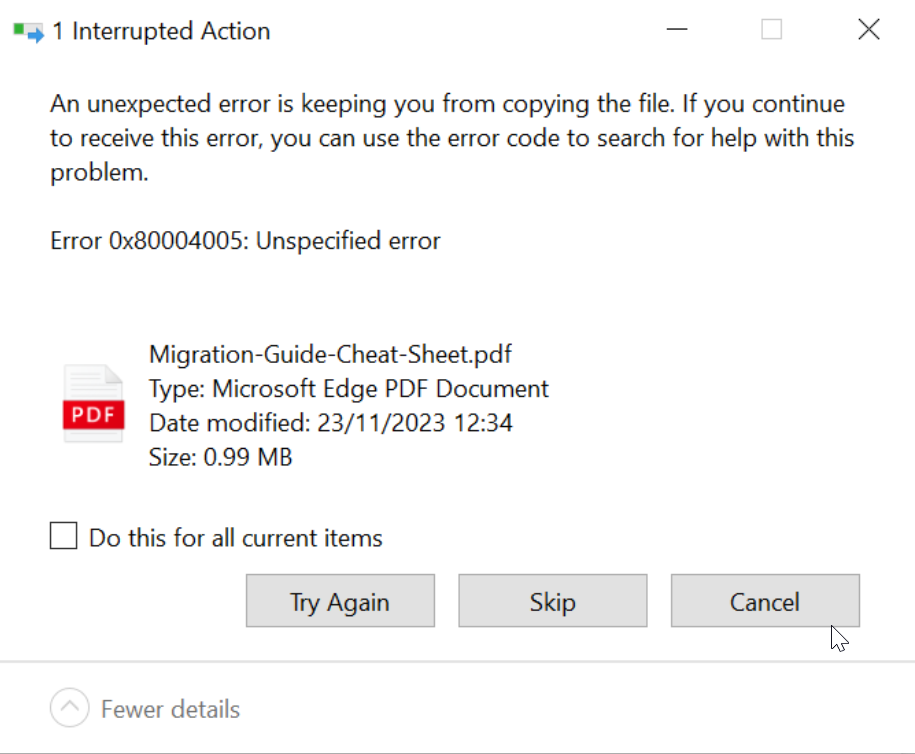
Should you see an error message, such as “An unexpected error is keeping you from copying the file…” with an error code like 0x80004005, this indicates a problem that could be due to trying to extract an AES-256 encrypted ZIP without appropriate software.
For AES-256 Encrypted ZIP Files Using 7-Zip:
- Right-Click the Encrypted ZIP File: In your file explorer, locate your AES-256 encrypted ZIP file, right-click on it to bring up the ‘context menu’ or ‘file options’ list
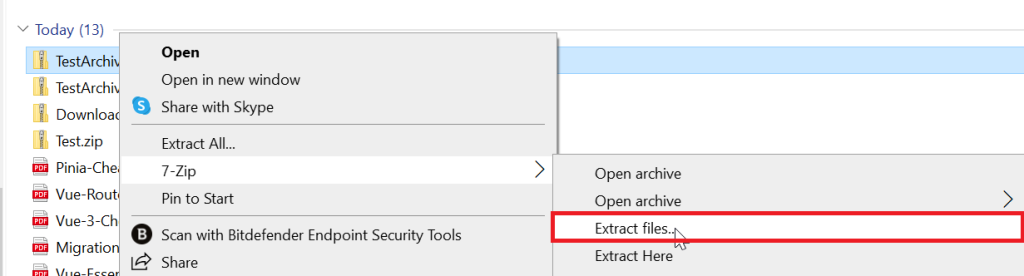
7Zip File Extraction GUI will open…
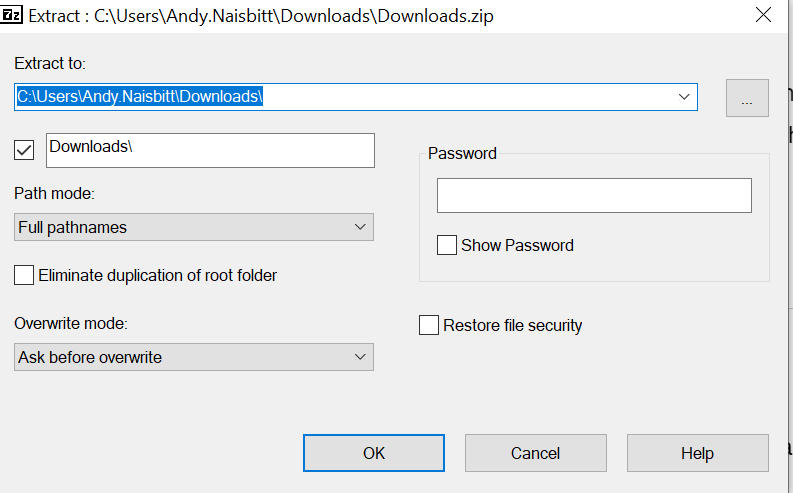
2. Set Extraction Parameters: In the extraction window, choose where to extract the files, and enter the password when prompted.
3. Extract: Click ‘OK’ to begin the extraction process. Once extracted, navigate to the specified destination to access your files.
Remember, for enhanced security with AES-256 encryption, third-party software like 7-Zip or WinRAR is required as Windows File Explorer does not natively support extracting these files.
Navigating the Security Landscape of 7-zip
When it comes to 7-Zip, the murmurs about security gaps do pop up now and again—no surprise there, as this is a common scene across the software board. However, the folks behind 7-Zip aren’t ones to drag their feet; they tackle these vulnerabilities with a commendable quickness. It’s this agility in response that gives users a solid piece of mind.
What really sets 7-Zip apart is its open-source badge of honor. This isn’t just about transparency; it’s about inviting the world to take a peek under the hood—security analysts included. And they do, sifting through the code with a fine-tooth comb, ensuring any kinks are ironed out posthaste.
As for its Russian roots, that’s more a topic for the political stage than a user’s primary concern. The code speaks louder than geopolitical whispers, and in the language of security, it’s been pretty fluent.
Keeping your 7-Zip updated is akin to keeping your digital doors locked tight—basic but effective. And for those who like to double-down on their security measures, a bit of personal due diligence goes a long way. Scrutinize the source code, stay in the loop with the latest updates, and keep your ears to the ground for any whispers of concern. For the IT Admins who stand guard over their networks, here’s a toolkit for your arsenal—links that’ll keep you informed and ahead of the curve:
- Link to 7-Zip’s official update log
- Link to community forums for real-time user feedback
- Link to the repository for the truly diligent who want to review the source
With these resources at your fingertips, you can navigate the waves of software security with the finesse of a seasoned sailor. Remember, the key to using 7-Zip safely is as much in its robust framework as in your vigilant management.
Alternatives to 7-Zip: For those seeking different options, tools like WinRAR, WinZip, and the Nanazip fork of 7-Zip, as well as PeaZip, offer similar functionalities.
7-Zip remains a strong, viable option for file compression and encryption. Its open-source nature and consistent updates make it a reliable tool for securing your data.
In today’s digital age, where data security is paramount, encryption stands as a formidable shield against potential threats. As we’ve explored in our comprehensive guide on ‘7-Zip Password Protection,’ encryption is a vital component of safeguarding your sensitive information. However, in this rapidly evolving landscape, it’s crucial to delve even deeper into the world of encryption to understand its broader implications and the latest trends.
In this post, we’ll explore the overarching importance of encryption in 2023, its various types, and the most advanced encryption methods that businesses need to employ to stay ahead of evolving threats. We’ll also address the potential pitfalls of outdated encryption and security protocols while diving into the advantages and disadvantages of end-to-end encrypted messages. Finally, we’ll glimpse into the future and examine the key security trends shaping the world of encryption and what might eventually replace it.
So, let’s embark on this journey to unravel the critical role encryption plays in securing your data in the digital age.
Join Our Community!
🌟 Get exclusive insights and the latest IT tools and scripts, straight to your inbox.
🔒 We respect your privacy. Unsubscribe at any time.